Azure has a lot of network products and features, I will try to cover most important Features.
The components offered by Azure Virtual Network are:
Virtual Networks - Using Microsoft Azure Virtual Networks, you can deploy Azure services such as infrastructure Virtual Machine (IaaS), Redis Cache, and Web Apps. Each Virtual Network can have more than one overarching address space defined, and is subdivided into one or more subnets.
Network Security Groups - These are essentially Layer 4 (OSI model) firewall rules that allow you to limit the flow of network traffic at the Subnet and individual Network Interface layers. Each Network Security Group can contain up to 200 individual Network Security Rules, which allow or deny traffic, based on a variety of parameters, such as the source / destination IP address and ports, the network protocol, rule priority, and others. Network Security Groups must be created in the same Azure Region (Location) as the Virtual Network subnet that it will be associated with.
VPN Gateway - Using Microsoft Azure VPN Gateway, you can securely connect globally-distributed Virtual Networks together, as well as extending on-premises networks into the cloud. This scenario is known as Site-to-Site (S2S) connectivity, and is also commonly called "hybrid networking." You can also enable Point-to-Site (P2S) connectivity, where the "point" is a client device that connects directly to the Virtual Network, and and enables private access to network resources over a secure Virtual Private Network (VPN) connection. The P2S model is particularly useful for deploying lab environments in Microsoft Azure, that are only accessible through a private interface, or other cloud-based workloads that don't require public access.
Load Balancer - Using the Microsoft Azure Load Balancer, you can build and deploy geographically distributed, high performance, highly available applications. Load Balancers can be exposed publicly, through the use of a Public IP Address resource, or they can simply be deployed into a Virtual Network subnet for private, internal access. The Load Balancer health probe ensures the availability and health of the application, on each endpoint. Endpoints are dynamically added and removed from the Load Balancer's rotation.
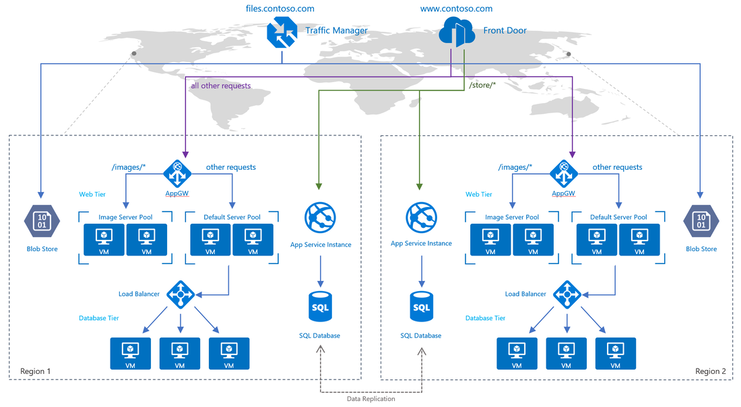
Traffic Manager - Load Balancer for geographically distributed Datacenters. Azure Traffic Manager uses DNS to redirect requests to an appropriate geographical location endpoint. Traffic Manager does not see the traffic passing between the client and the service. It simply redirects the request based on most appropriate endpoints
Use case: load between two endpoints where your first endpoint is in Azure and second endpoint placed in on-premise datacenter
Application Gateway - Application Gateway uses Azure Load Balancer at the transport level and then applies the routing rules to support layer-7 ( HTTP) load balancing.
Application Gateway currently supports the following:
1- HTTP load- balancing
2- SSL termination
3- Cookie based session affinity
The primary use cases for Application Gateway are :
Content Delivery Network (CDN) - A content delivery network (CDN) is a system of distributed servers (network) that deliver pages and other Web content to a user, based on the geographic locations of the user, the origin of the webpage and the content delivery server.
Mechanism: Servers nearest to the website visitor respond to the request. The content delivery network copies the pages of a website to a network of servers that are dispersed at geographically different locations, caching the contents of the page. When a user requests a webpage that is part of a content delivery network, the CDN will redirect the request from the originating site's server to a server in the CDN that is closest to the user and deliver the cached content. CDNs will also communicate with the originating server to deliver any content that has not been previously cached
Virtual WAN - Azure Virtual WAN is a networking service that provides optimized and automated branch-to-branch connectivity through Azure.
Virtual WAN provides large-scale site-to-site connectivity and is built for throughput, scalability, and ease of use. ExpressRoute and point-to-site connectivity functionality is currently under Preview. CPE branch devices auto-provision and connect into Azure Virtual WAN. These devices are available from a growing ecosystem of SD-WAN and VPN partners
Peering - By default Azure VNETs can't communicate to each other unless you configure Peering between VNETs.
Virtual network peering enables you to seamlessly connect two Azure virtual networks. Once peered, the virtual networks appear as one, for connectivity purposes. The traffic between virtual machines in the peered virtual networks is routed through the Microsoft backbone infrastructure, much like traffic is routed between virtual machines in the same virtual network, through private IP addresses only. Azure supports:
Route Tables - Microsoft Azure Virtual Networks support custom Route Tables, allowing you to shape the flow of cloud-based network traffic. One of the more common use cases of custom Route Tables is to route all network traffic through a Virtual Appliance that is responsible for ensuring the security of network traffic. A Route Table can be created, by itself, directly inside an ARM Resource Group, but it must be associated with a Virtual Network subnet in order to take effect on network traffic.
The components offered by Azure Virtual Network are:
Virtual Networks - Using Microsoft Azure Virtual Networks, you can deploy Azure services such as infrastructure Virtual Machine (IaaS), Redis Cache, and Web Apps. Each Virtual Network can have more than one overarching address space defined, and is subdivided into one or more subnets.
Network Security Groups - These are essentially Layer 4 (OSI model) firewall rules that allow you to limit the flow of network traffic at the Subnet and individual Network Interface layers. Each Network Security Group can contain up to 200 individual Network Security Rules, which allow or deny traffic, based on a variety of parameters, such as the source / destination IP address and ports, the network protocol, rule priority, and others. Network Security Groups must be created in the same Azure Region (Location) as the Virtual Network subnet that it will be associated with.
VPN Gateway - Using Microsoft Azure VPN Gateway, you can securely connect globally-distributed Virtual Networks together, as well as extending on-premises networks into the cloud. This scenario is known as Site-to-Site (S2S) connectivity, and is also commonly called "hybrid networking." You can also enable Point-to-Site (P2S) connectivity, where the "point" is a client device that connects directly to the Virtual Network, and and enables private access to network resources over a secure Virtual Private Network (VPN) connection. The P2S model is particularly useful for deploying lab environments in Microsoft Azure, that are only accessible through a private interface, or other cloud-based workloads that don't require public access.
Load Balancer - Using the Microsoft Azure Load Balancer, you can build and deploy geographically distributed, high performance, highly available applications. Load Balancers can be exposed publicly, through the use of a Public IP Address resource, or they can simply be deployed into a Virtual Network subnet for private, internal access. The Load Balancer health probe ensures the availability and health of the application, on each endpoint. Endpoints are dynamically added and removed from the Load Balancer's rotation.
Traffic Manager - Load Balancer for geographically distributed Datacenters. Azure Traffic Manager uses DNS to redirect requests to an appropriate geographical location endpoint. Traffic Manager does not see the traffic passing between the client and the service. It simply redirects the request based on most appropriate endpoints
Use case: load between two endpoints where your first endpoint is in Azure and second endpoint placed in on-premise datacenter
Application Gateway - Application Gateway uses Azure Load Balancer at the transport level and then applies the routing rules to support layer-7 ( HTTP) load balancing.
Application Gateway currently supports the following:
1- HTTP load- balancing
2- SSL termination
3- Cookie based session affinity
The primary use cases for Application Gateway are :
- If your application requires session affinity as an example the clients want to reach same backend virtual machine.
- If your web servers do not want to handle the SSL overhead and you require the manage the SSL termination at the gateway.
- If your application requires multiple HTTP request on the same TCP connection to be load balance on the different backend virtual machines
Content Delivery Network (CDN) - A content delivery network (CDN) is a system of distributed servers (network) that deliver pages and other Web content to a user, based on the geographic locations of the user, the origin of the webpage and the content delivery server.
Mechanism: Servers nearest to the website visitor respond to the request. The content delivery network copies the pages of a website to a network of servers that are dispersed at geographically different locations, caching the contents of the page. When a user requests a webpage that is part of a content delivery network, the CDN will redirect the request from the originating site's server to a server in the CDN that is closest to the user and deliver the cached content. CDNs will also communicate with the originating server to deliver any content that has not been previously cached
Virtual WAN - Azure Virtual WAN is a networking service that provides optimized and automated branch-to-branch connectivity through Azure.
- Connect any number of branches with multiple connections
- Auto provisioning from branch office to Azure
- Automated configuration download and connection enablement
- Built for throughput and scalability
- Unified monitoring and management CPE branch devices managed by a growing ecosystem of SD-WAN and VPN partners
Virtual WAN provides large-scale site-to-site connectivity and is built for throughput, scalability, and ease of use. ExpressRoute and point-to-site connectivity functionality is currently under Preview. CPE branch devices auto-provision and connect into Azure Virtual WAN. These devices are available from a growing ecosystem of SD-WAN and VPN partners
Peering - By default Azure VNETs can't communicate to each other unless you configure Peering between VNETs.
Virtual network peering enables you to seamlessly connect two Azure virtual networks. Once peered, the virtual networks appear as one, for connectivity purposes. The traffic between virtual machines in the peered virtual networks is routed through the Microsoft backbone infrastructure, much like traffic is routed between virtual machines in the same virtual network, through private IP addresses only. Azure supports:
- VNet peering - connecting VNets within the same Azure region
- Global VNet peering - connecting VNets across Azure regions
Route Tables - Microsoft Azure Virtual Networks support custom Route Tables, allowing you to shape the flow of cloud-based network traffic. One of the more common use cases of custom Route Tables is to route all network traffic through a Virtual Appliance that is responsible for ensuring the security of network traffic. A Route Table can be created, by itself, directly inside an ARM Resource Group, but it must be associated with a Virtual Network subnet in order to take effect on network traffic.