|
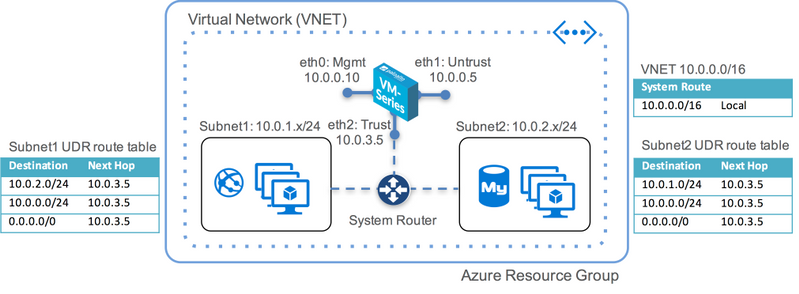
In this post I will explain how to create a user-defined route and route your resources traffic through it. This guide will be very helpful specially if you have a network or security appliance deployed on azure or even on-prem. First of all, you have to know that Azure automatically creates a route table for each subnet within an Azure virtual network and adds system default routes to the table We have two main type of routes on Azure:
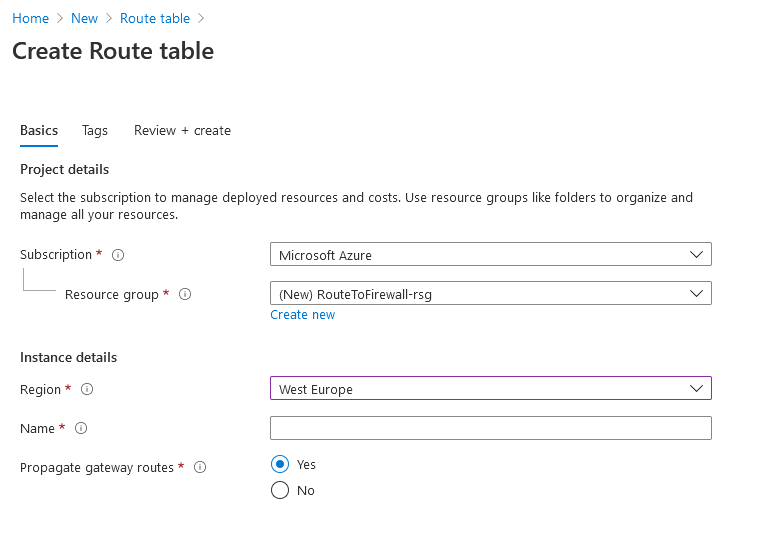
Now, let’s create a route table on azure and route resources traffic into the Palo Alto Firewall (I have deployed it before) through the UDR 1- Login to Azure Portal 2- From Home > Click on Create A Resource 3- Search for Route Table 4- Select it then click on Create and configure the following settings:
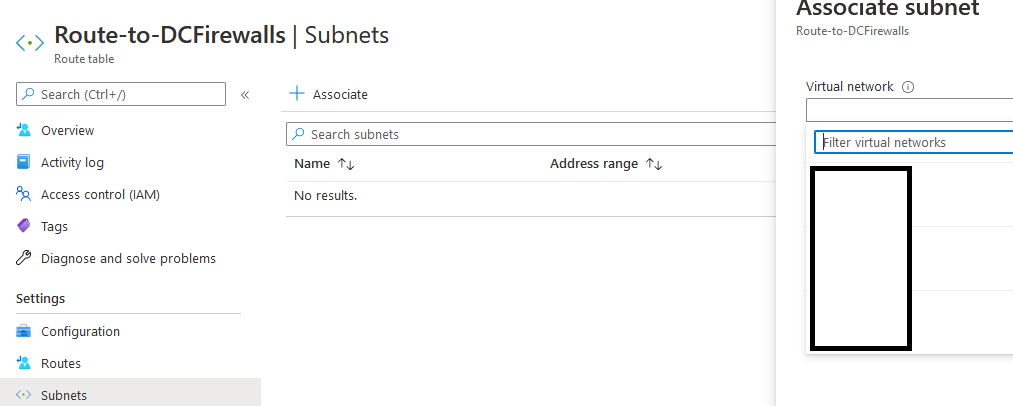
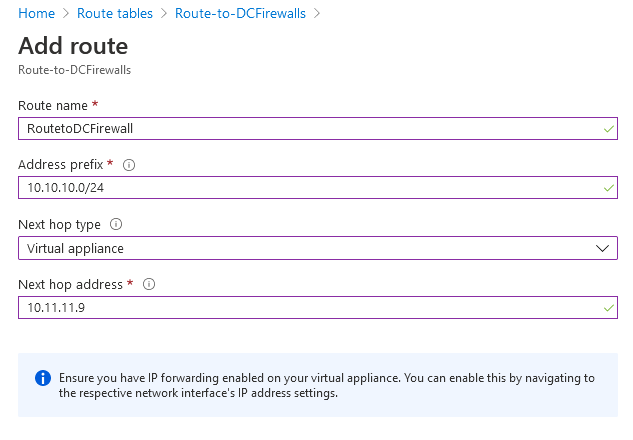
Now let's Consider that your Virtual Applicance "in my case Palo Alto Firewall" has the IP "10.11.11.9" 5- The most important parts in the route table is the Subnet & and Routes 6- Select Subnet column, then Click on Associate
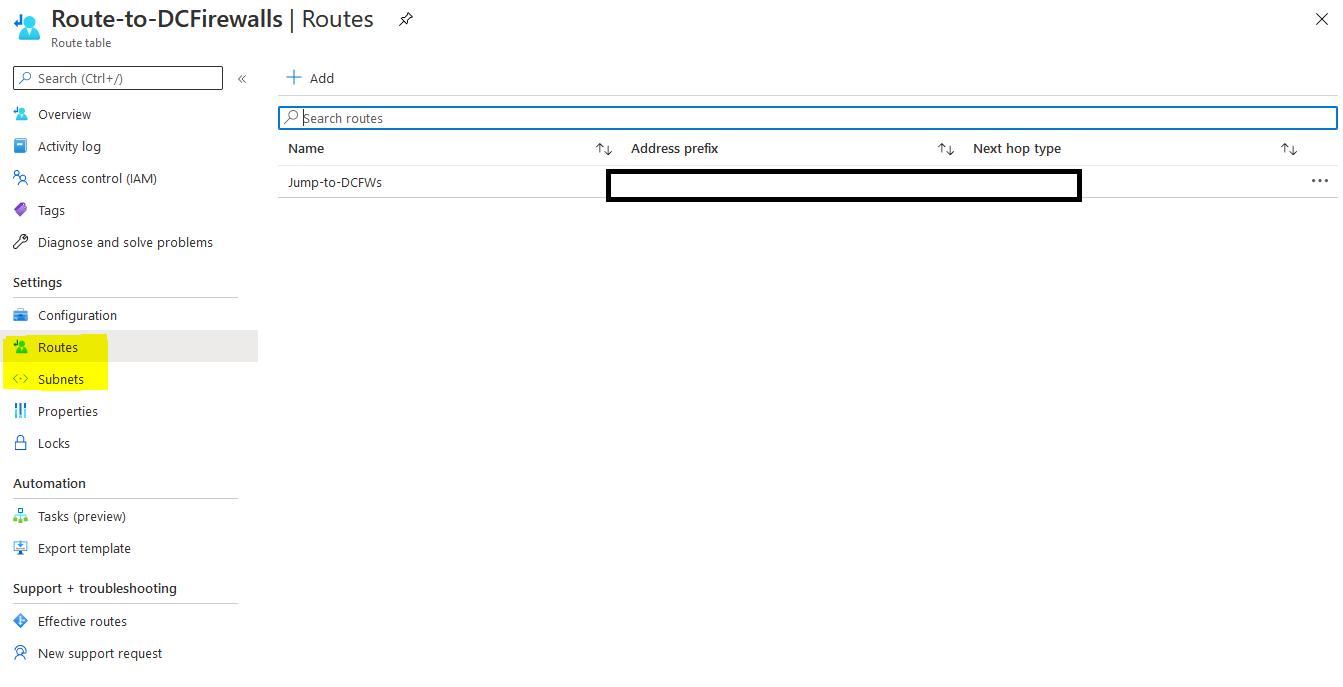
The subnets associated with this route table are now visible in the subnets section of your route tables column IF you have any VM running on Azure you must restart it in order to update the route, or you can run the below commands on the VM netsh winsock reset netsh int IP reset ipconfig /flushdns Note: After associating the sbunet your VMs might not be accessible anymore! unless you de-associate the subnet, so we recommend to add the routing and test it on a testing VM then start associating the Subnets. 7- and let's Add Route, from Settings column, click Routes 8- In the Routes column, click + Add In the Add route column, configure the following settings:
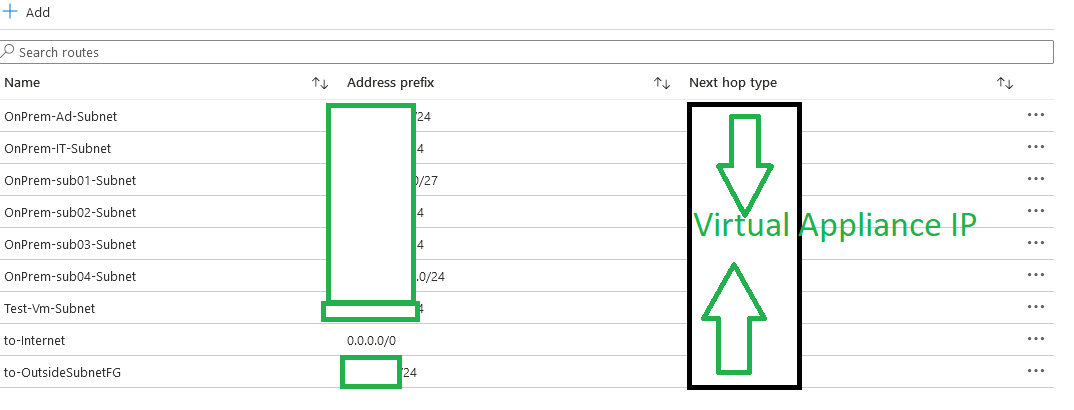
Finally, I want you to focus on the Rotues coulmn as it's the most import field when we talk about UDR. Let's consider that you have have a vNet on a different subscription or even on-prem so how you can forward the traffic into your virtual applicance? I will show you an example: By adding the Routes with the subnet in the Route table you will be able to reach the virtual appliane from differnet subscription or from On-Prem servers.
2 Comments
Bryan
3/29/2022 02:37:16 am
Good article. Any suggestions on how you route the management interface through the vpn if you have panorama on premise? I assume this could be UDR?
Reply
Rousan
3/30/2022 01:44:31 am
Hi Bryan,
Reply
Leave a Reply. |
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|


 RSS Feed
RSS Feed
