|
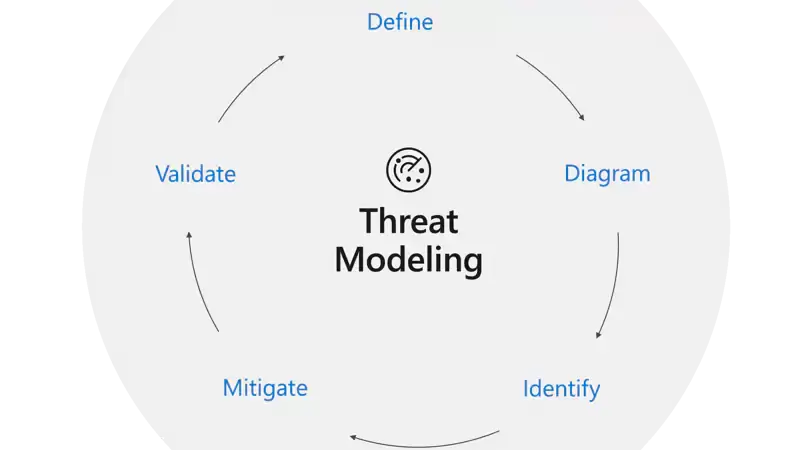
This article in our series focused on Microsoft’s free security tools is on the Security Development Lifecycle (SDL) Threat Modeling Tool. Threat modeling is a core element of the Microsoft Security Development Lifecycle (SDL). It’s an engineering technique you can use to help you identify threats, attacks, vulnerabilities, and countermeasures that could affect your application. You can use threat modeling to shape your application's design, meet your company's security objectives, and reduce risk. Microsoft Threat Modeling Tool The Microsoft Threat Modeling Tool makes threat modeling easier for all developers through a standard notation for visualizing system components, data flows, and security boundaries. It also helps threat modelers identify classes of threats they should consider based on the structure of their software design. We designed the tool with non-security experts in mind, making threat modeling easier for all developers by providing clear guidance on creating and analyzing threat models There are five major threat modeling steps:
Threat modeling is not a one-time process, it should be iterative starting early in the application development and continuing throughout its lifecycle. This is because it is difficult to identify all potential threats in a single pass, and applications change over time to accommodate evolving business requirements, requiring the threat modeling process to be repeated. Whether you use the SDL or not, this tool is still useful for understanding threats to a networked system. Some of the tool's key capabilities and innovations include:
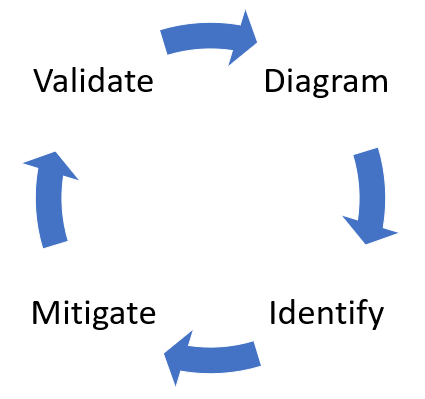
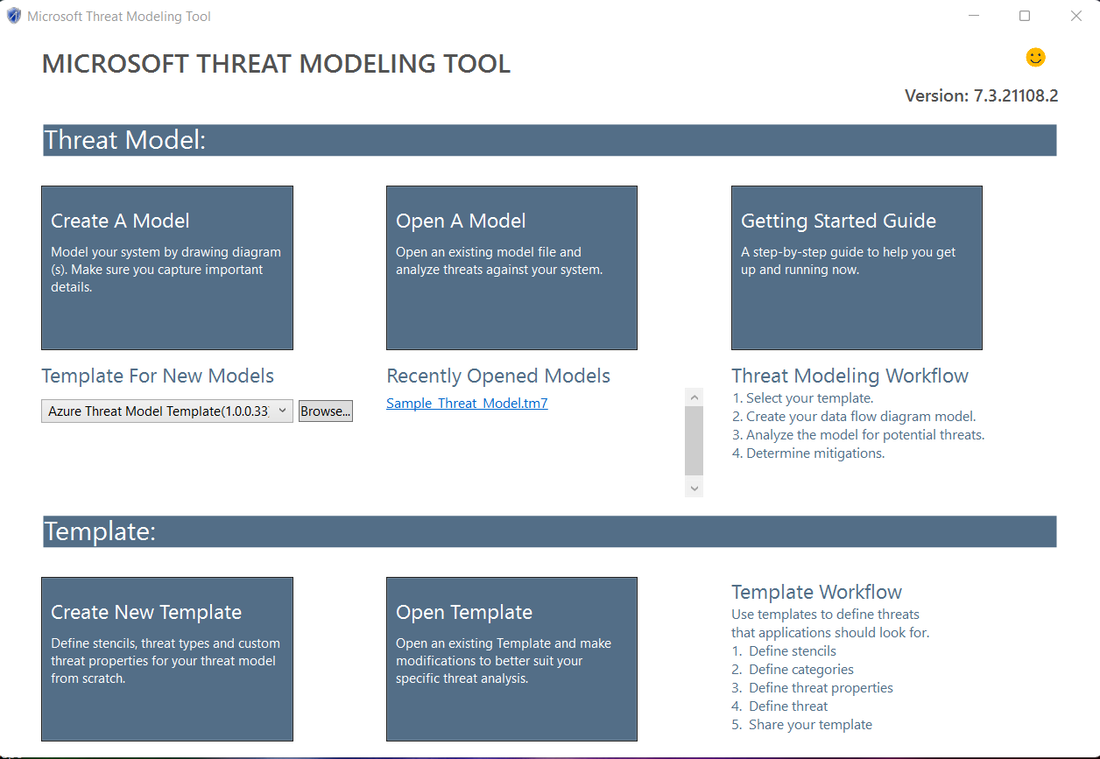
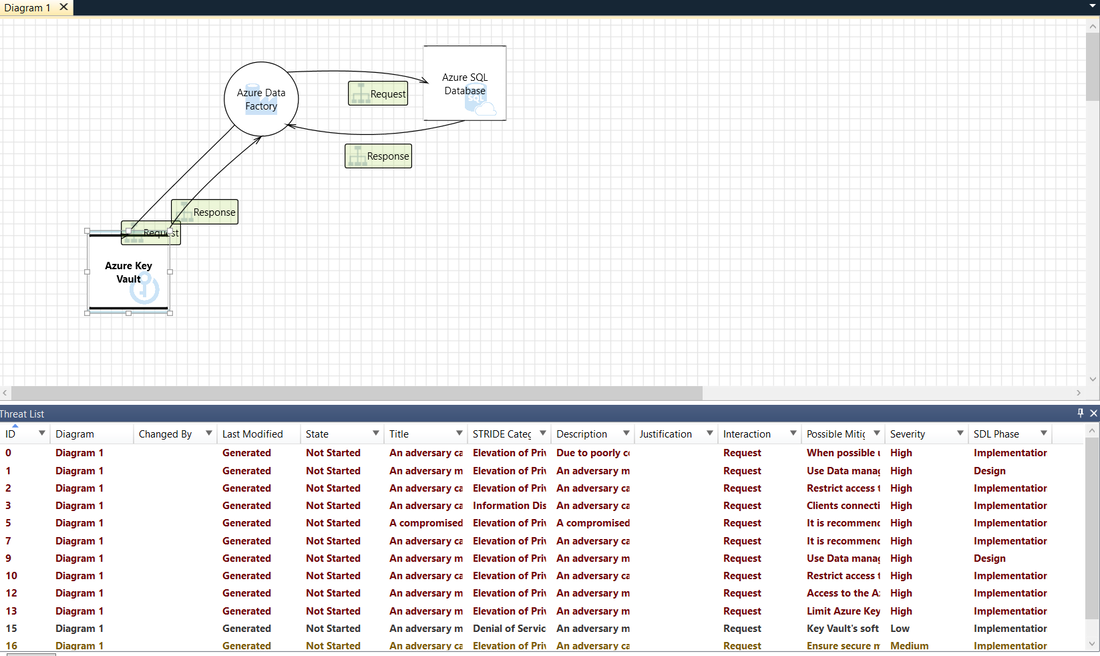
To quickly summarize, the approach involves creating a diagram, identifying threats, mitigating them and validating each mitigation. Here’s a diagram that highlights this process: Starting the threat modeling process 1- Run the tool 2- Click on Create a Model 3- Start Building a model Note: you can end users/developers or web access/request 4- Click on Data flow icon 5- Analyzing threats Once he clicks on the analysis view from the icon menu selection (file with magnifying glass), he is taken to a list of generated threats the Threat Modeling Tool found based on the default template, which uses the SDL approach called STRIDE (Spoofing, Tampering, Info Disclosure, Repudiation, Denial of Service and Elevation of Privilege). The idea is that software comes under a predictable set of threats, which can be found using these 6 categories This article explains the reason for not discussing assets in the threat modeling process. It is noted that many software engineers have a better understanding of their software than of the concept of assets and what assets an attacker may target.
Similar to threat modeling a house, you can start by thinking about your family, precious possessions, or valuable artwork. Alternatively, you can focus on potential intruders and the security system, or physical features such as the pool or front porch. These are equivalent to considering assets, attackers, or software design in threat modeling. Any of these approaches can be effective. The software design approach to threat modeling presented in this article is simpler compared to previous methods by Microsoft. This approach has been found to work well for many teams and it is hoped that it will be useful for yours as well.
0 Comments
Leave a Reply. |
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|


 RSS Feed
RSS Feed
