|
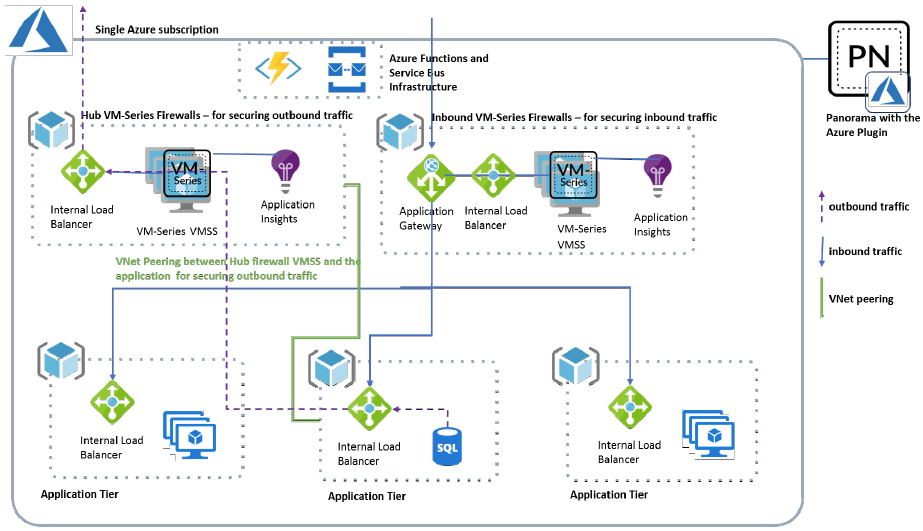
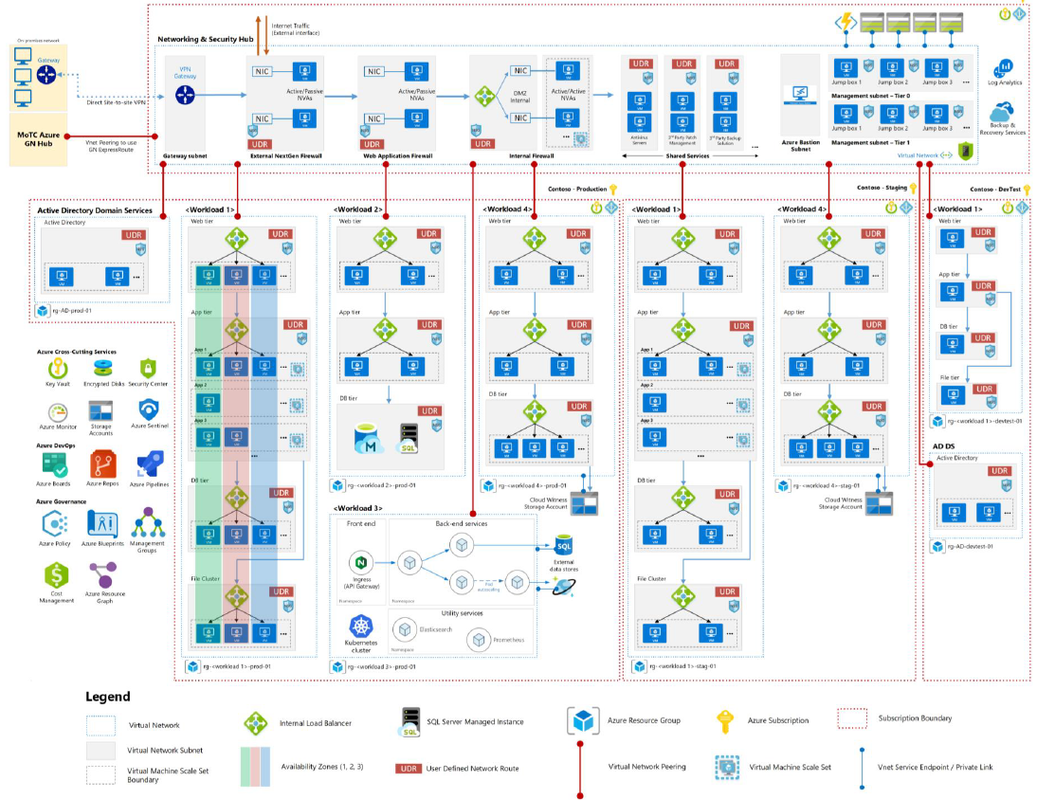
One of my customers has requested to deploy HA Palo Alto Firewalls on Azure, and since that time I suffered multiple time as I didn't find enough resources explaining the same so I decided to write this post and share my experience with everyone Before I start I will explain the current Azure architecture Design I have. The below design explaining Microsoft best practices for deploying resources across Subscriptions and VNETs read more : https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/migrate/azure-best-practices/migrate-best-practices-networking Assumptions and Prerequisites:
Virtual Network I have Created Three VNETs
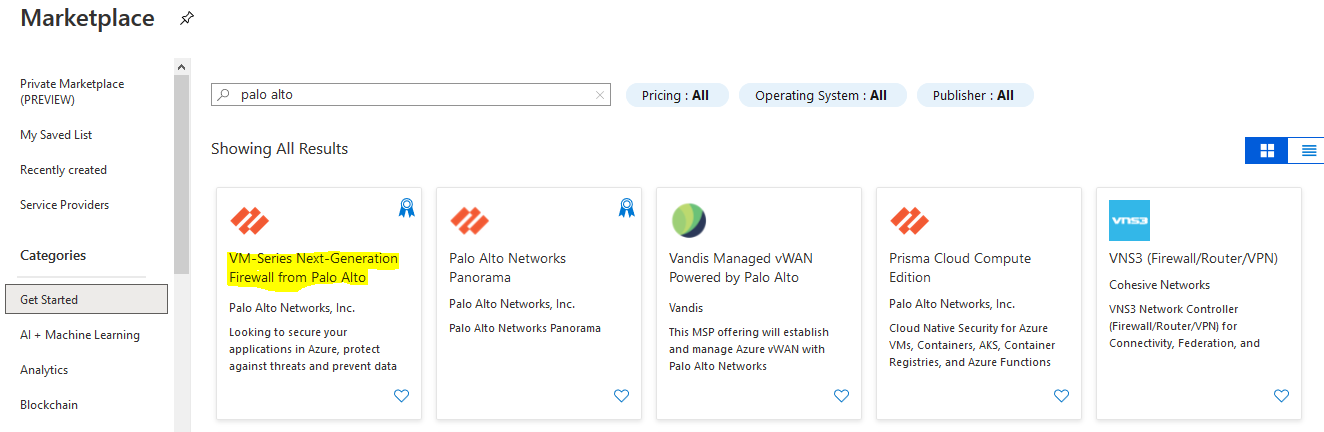
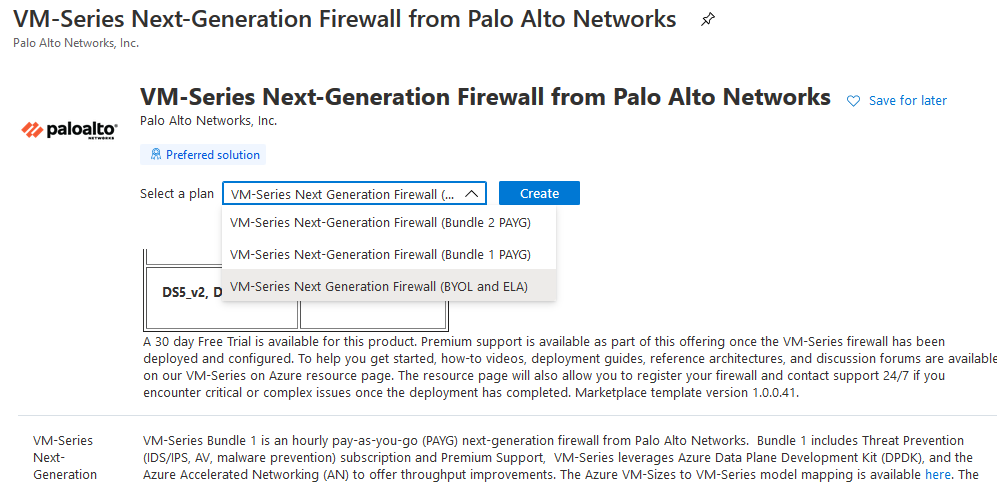
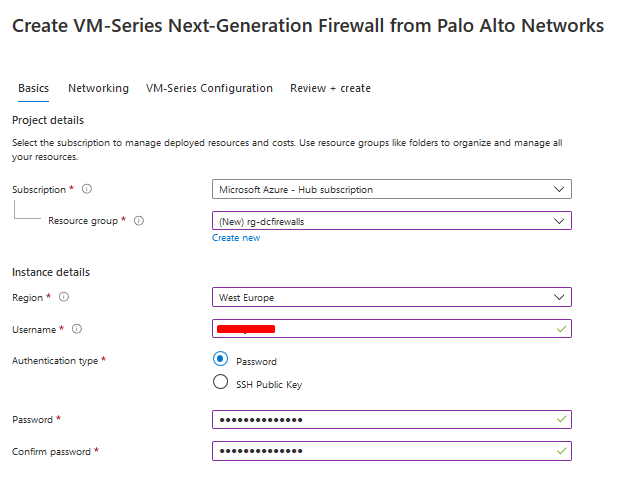
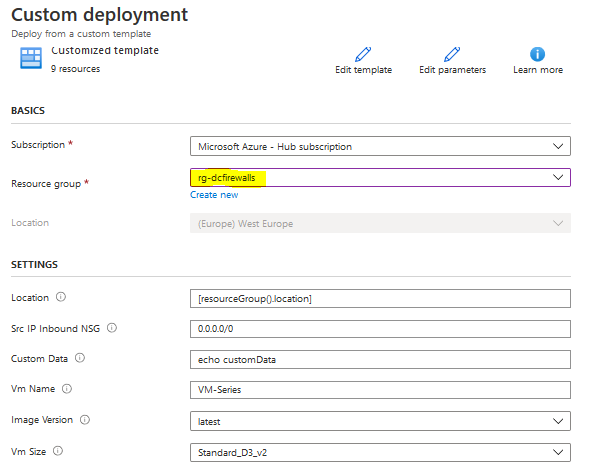
I have deployed the firewalls on Hub-subscription, while I have deployed the whole resources on Res-Subscription This is an awesome post that covers best practices for network design, hub/spoke networking, perimeter security, and a lot more Read More Deployment 1- Login to Azure Portal 2- Go To Azure Market Place and search for "VM-Series Next-Generation Firewall from Palo Alto" 3- You have to select the Plan - in my case the customer already have the licenses so I will select (BYOL) Software plan -VM-Series Next-Generation Firewall (Bundle 2 PAYG) VM-Series Bundle 2 is an hourly pay-as-you-go (PAYG) Palo Alto Networks next-generation firewall. Bundle 2 includes URL Filtering, WildFire, GlobalProtect, DNS Security subscriptions, and Premium Support. VM-Series leverages Azure Data Plane Development Kit (DPDK), and the Azure Accelerated Networking (AN) to offer throughput improvements. The Azure VM-Sizes to VM-Series model mapping is available here. The pricing is as follows Azure VM Sizes <-> Hourly Price
-VM-Series Next-Generation Firewall (Bundle 1 PAYG) VM-Series Bundle 1 is an hourly pay-as-you-go (PAYG) next-generation firewall from Palo Alto Networks. Bundle 1 includes Threat Prevention (IDS/IPS, AV, malware prevention) subscription and Premium Support, VM-Series leverages Azure Data Plane Development Kit (DPDK), and the Azure Accelerated Networking (AN) to offer throughput improvements. The Azure VM-Sizes to VM-Series model mapping is available here. The pricing is as follows Azure VM Sizes <-> Hourly Price
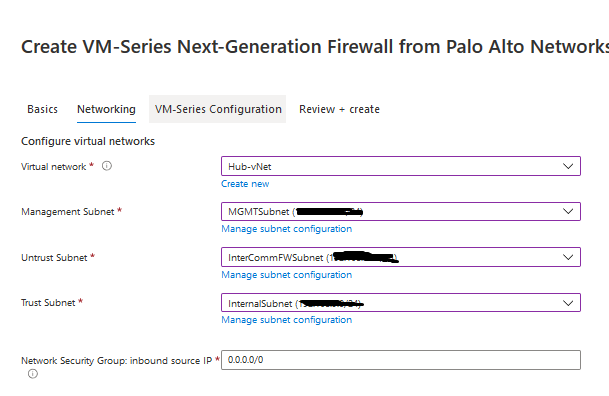
-VM-Series Next Generation Firewall (BYOL and ELA) The VM-Series next-generation firewall from Palo Alto Networks allows developers and cloud security architects to embed inline threat and data loss prevention into their application development workflows. Native Azure services combined with VM-Series automation features allow you to create "touchless" deployments using bootstrapping and enables your developers to operate at the speed of the cloud. Your applications and data are protected with whitelisting and segmentation policies that are dynamically updated based on Azure tags assigned to workloads, allowing you to reduce the attack surface area and achieve compliance. Additionally, Threat Prevention policies can stop both known and unknown attacks. The VM-Series BYOL listing also supports Enterprise Licensing Agreement (ELA) for combining VM-Series next-generation firewall and subscription bundles that are appropriate for your needs. Panorama (available separately in Marketplace) allows the VM-Series to be managed centrally alongside our firewall appliances to maintain security policy that is consistent with on-premises environments. Note: With PAN-OS 9.1.0 VM-Series now supports DPDK in addition to previously supported Azure Accelerated Networking (AN) to efficiently process traffic and offer increased performance. To help you get started with your deployment, please visit our VM-Series on Azure resource page to access how-to videos, deployment guides, reference architectures and discussion forums. If you encounter critical or complex issues once the deployment has completed, please register your VM-Series and contact support 24/7. Marketplace template version 1.0.0.37. http://live.paloaltonetworks.com/azure 4- Click On Create Button 5- Start entering the configuration 6- For the network you have to select 3 VNETs
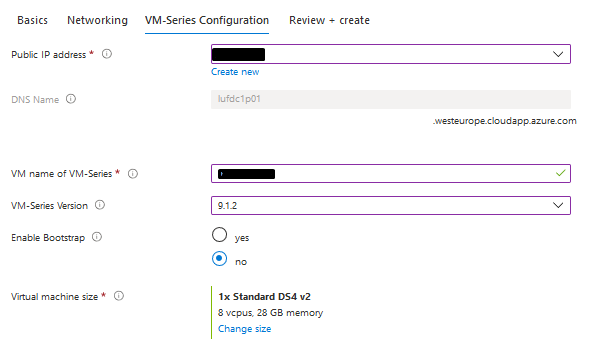
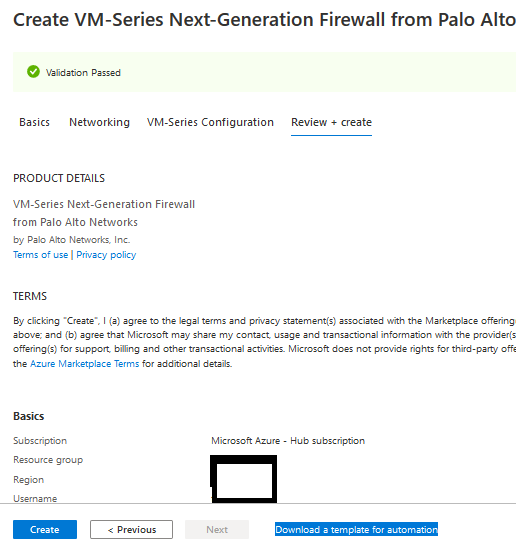
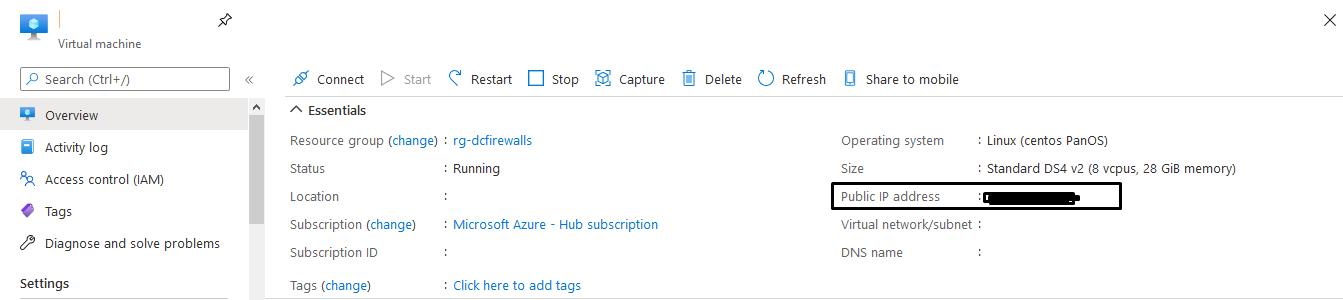
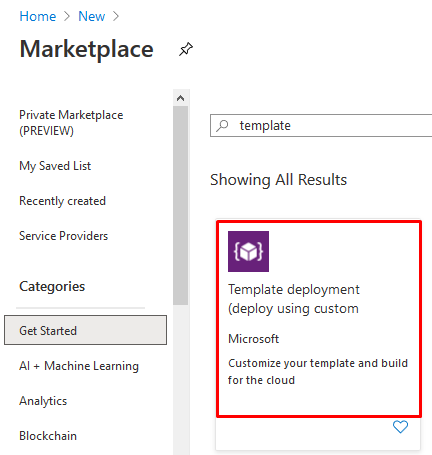
7- From "VM-Series Configuration" fill the DNS Name, Public IP Address and VM Size configuration 8- Click on next, then Create in order to provision the Node 9- And Once its complete you can test and access it using the public IP Address Deploy the Passive/Second Node As Palo Alto doesn't have a dedicated template to deploy the HA (Active/Passive) firewall as FortiGate, we have to deploy it manually The most important thing to consider when you deploy the Second/ Passive node is to place it on the SAME RESOURCE GROUP for Node1/Active Node 1- Go to Azure Market Place and select the same template 2- For the Resource Group select and temporary name as we will change it later 3- Complete the configuration part and DO NOT CLICK ON CREATE 4- Click on Download Template for Automation Word 5- Go To Market Place and search for "template" 6- Paste the content of the template there 7- Click On Deploy Button 8- Be Careful here as you have to change some Values and re-enter it again such As resource group, VNET, Subnets, etc 9-Make sure to select the same Resource group as the previous node 10- Once you finish, click on Deploy in order to start provision the new Node In Part Two, I Will explain the Post Configuration on The firewall from Azure Side and Palo Alto Site
6 Comments
Mina
10/11/2020 11:31:56 am
Amazing :)
Reply
Edor ghzabli
10/13/2020 06:24:51 pm
Kudos bro
Reply
nis
1/19/2022 12:54:16 am
Cant thank you enough...
Reply
Lou
9/27/2022 11:12:16 pm
The blueprint diagram is very blurry!
Reply
Ryan
8/5/2023 05:40:57 am
Can a Palo Alto firewall in azure be configured for dual stack? Any articles about HA for v4 and v6 in a PA FW in azure?
Reply
Leave a Reply. |
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|



 RSS Feed
RSS Feed
