|
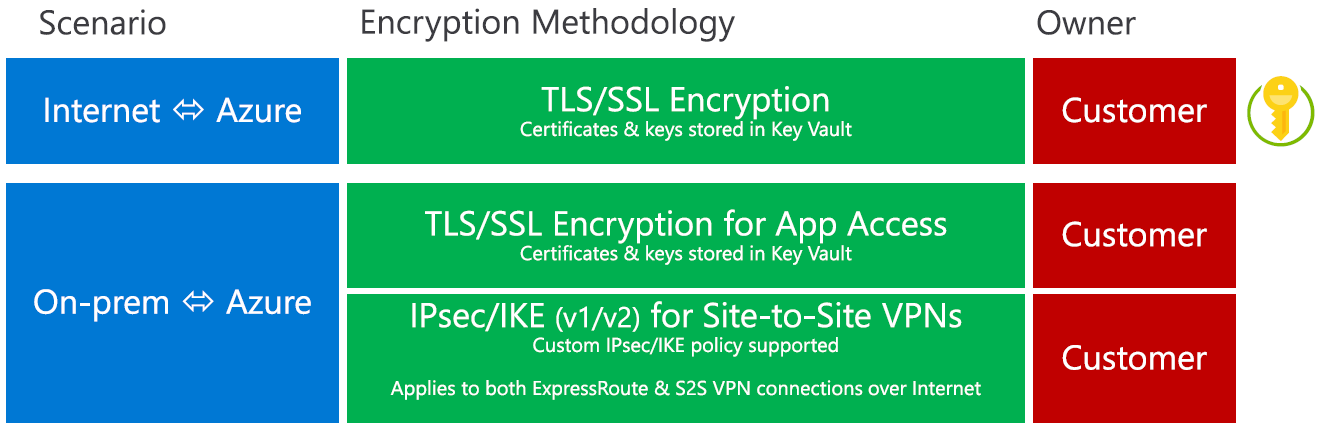
This guide will provides prescriptive guidance and deployment strategy, we will start this guide by explaining how to secure your data Secure control of data in Azure
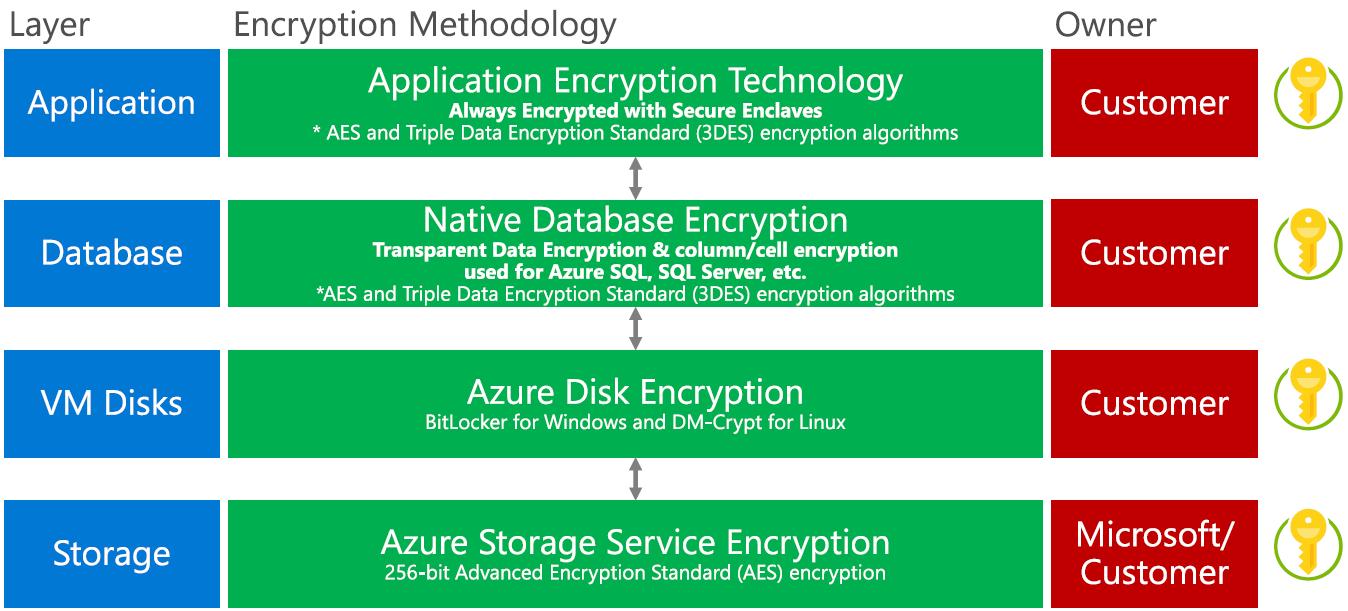
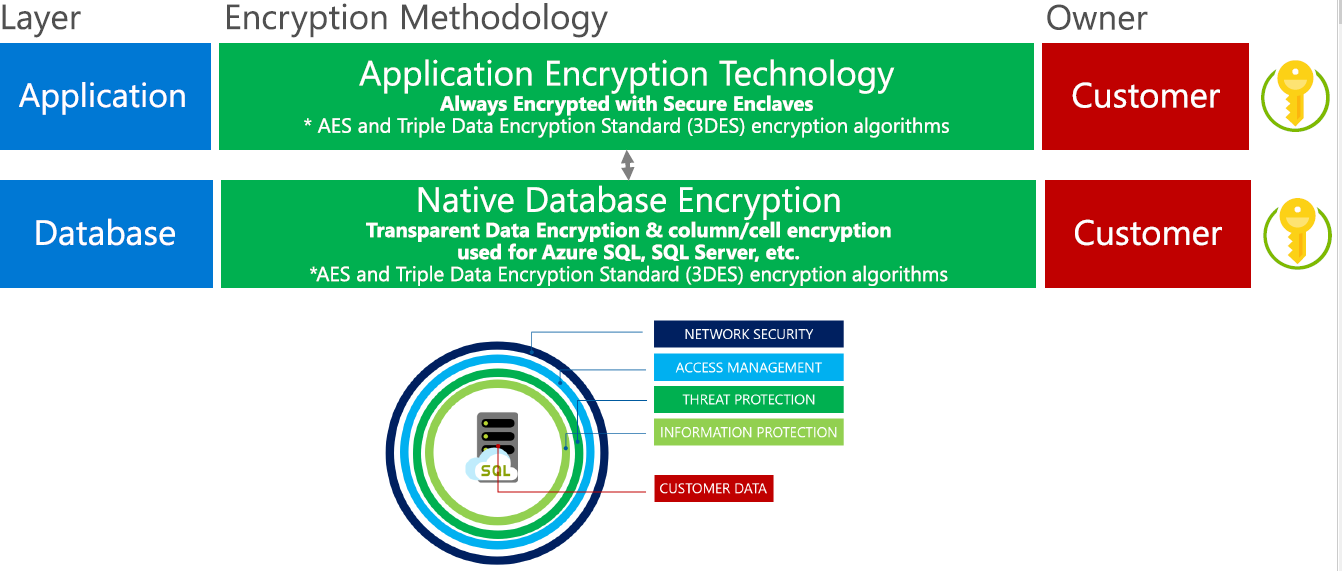
IaaS Encryption At Rest PaaS Encryption at Rest Encryption In Transit Encryption In Use
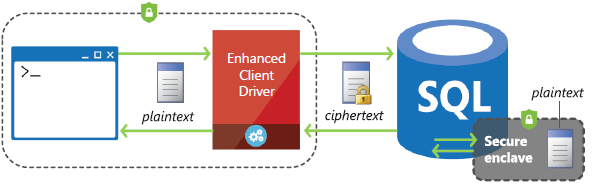
First public cloud to offer Intel Software Guard Extensions (SGX) enclaves
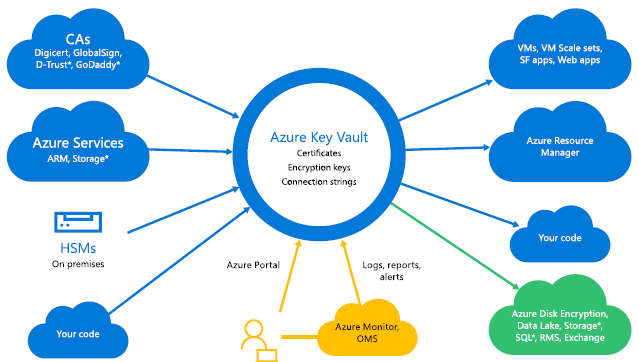
In-place encryption and key management Azure Key Vault Protect cryptographic keys with FIPS 140 2 Level 2 & Level 3 HSM by Thales Encrypt Azure VMs, Azure Data Lake, SQL Server, and other apps with a key in your key vault. The key never leaves the vault. Available as a service in every azure region Cost: Pay-as-you-go As security summary you have to:
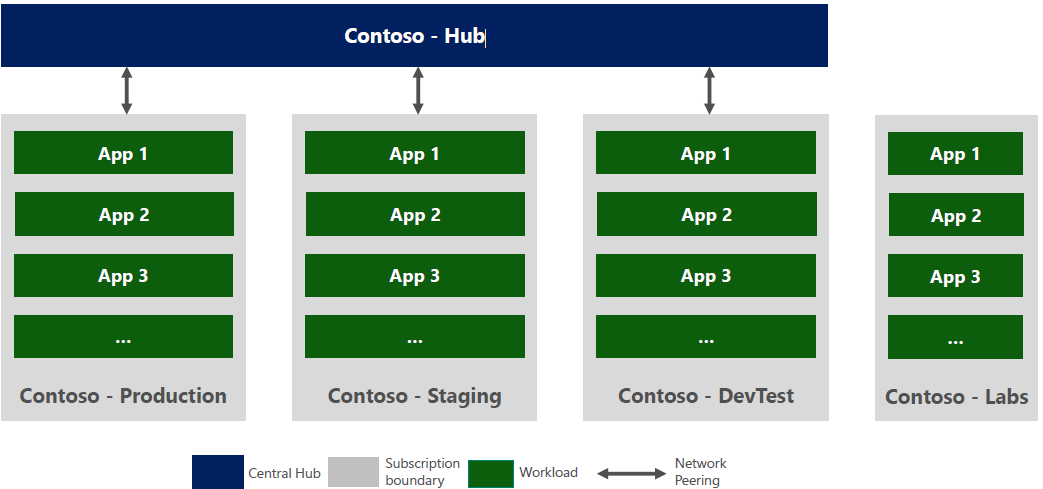
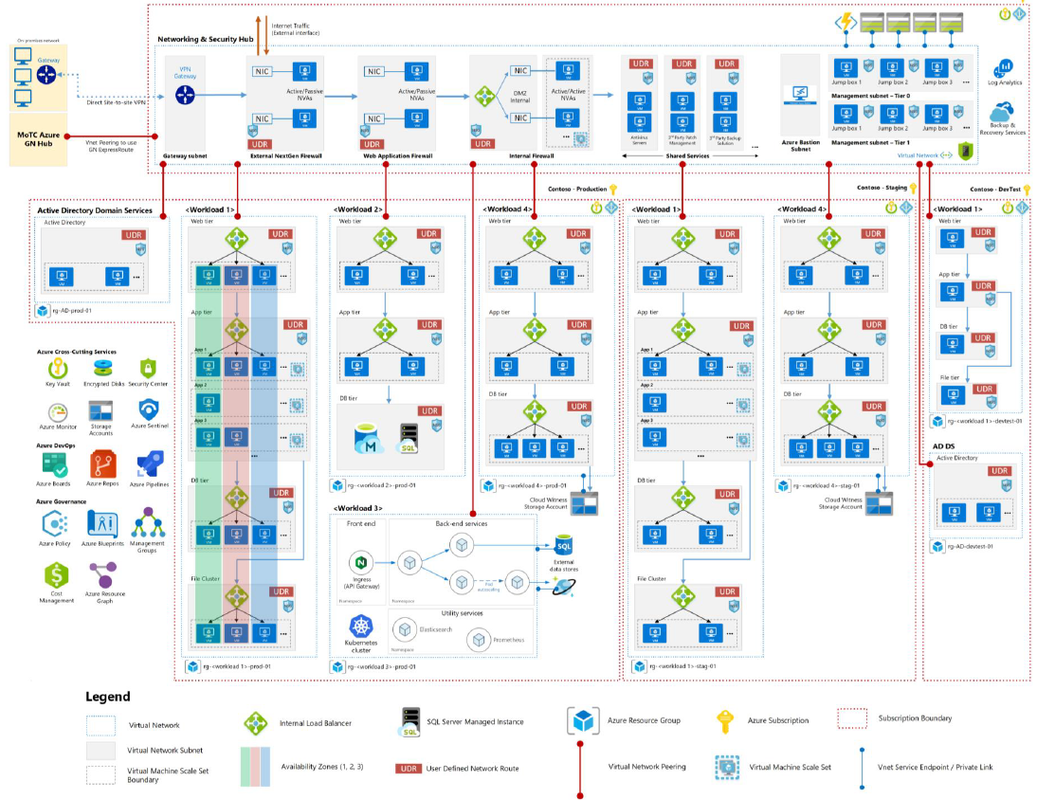
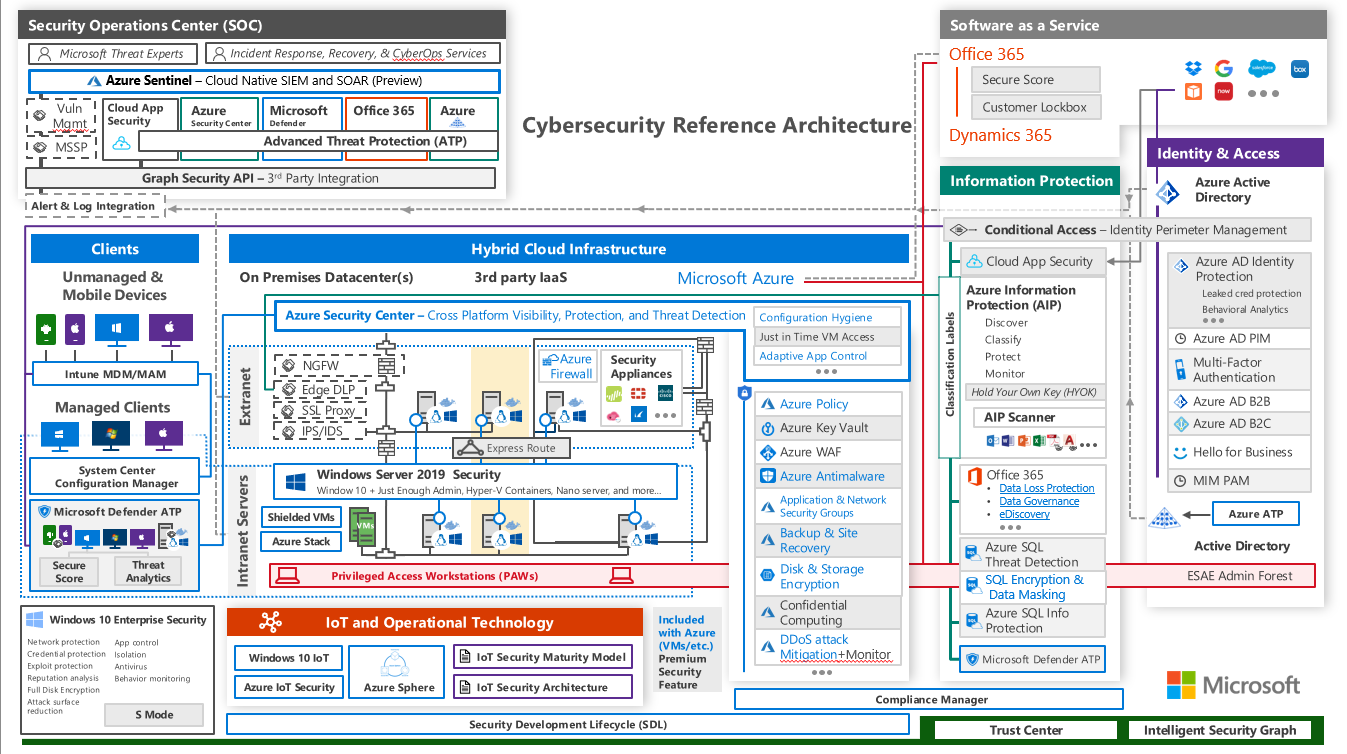
Subscription Structure Microsoft recommended to have a separated subscription for each workload such as Dev/Test and Production Azure Reference Architecture Microsoft Cybersecurity Reference Architecture References
1 Comment
|
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|




 RSS Feed
RSS Feed
