|
In this post, I want to show you how to configure terraform to use an Azure storage account to store and protect your tfstate file. To manage the infrastructure and configuration, Terraform writes the status of resources to a tfstate file. By default, this file is called “terraform. tfstate” and is stored locally in JSON format but can also store it remotely. It is created by Terraform the first time the terraform plan command is run and will use it each time it is run to compare its state with that of the target infrastructure and return the preview of the changes to be made Terraform state is used to reconcile deployed resources with Terraform configurations. State allows Terraform to know what Azure resources to add, update, or delete. This backend supports state locking and consistency checking with Azure Blob Storage native capabilities. By default, Terraform state is stored locally, which isn't ideal for the following reasons:
Note: By default the Azure Backend uses ADAL for authentication which is deprecated in favour of MSAL - MSAL can be used by setting use_microsoft_graph to true. The default for this will change in Terraform 1.2, so that MSAL authentication is used by default so, to create or manage azure resources from Azure DevOps pipeline, it's recommended to store the state file in Azure blob storage. But why? if you didn't store the state file (or if it get deleted) every time when you run the terraform Plan or Apply it will consider that you run it for the first time, so if in the first run create resource group in the second run it will give you runtime error "the resource is already exist!", hence you must store the state file in the storage. Also, it's recommended to create the storge outside terraform configuration, by using Azure CLI powershell, so if you run terraform destroy the storage will not be deleted :) so, let's create the storage Point to Consider:
Configure terraform backend stateTo configure the backend state, you need the following Azure storage information:
In case you decided to use access_key, microsoft recommended to store its value in Key vault or use environment variable by using a command similar to the following ACCOUNT_KEY=$(az storage account keys list --resource-group $RESOURCE_GROUP_NAME --account-name $STORAGE_ACCOUNT_NAME --query '[0].value' -o tsv) export ARM_ACCESS_KEY=$ACCOUNT_KEY Terraform Backend Configuration:
backend "azurerm" { resource_group_name = "StorageAccount-ResourceGroup" storage_account_name = "abcd1234" container_name = "tfstate" key = "prod.terraform.tfstate" use_msi = true subscription_id = "00000000-0000-0000-0000-000000000000" tenant_id = "00000000-0000-0000-0000-000000000000" } }
backend "azurerm" { storage_account_name = "abcd1234" container_name = "tfstate" key = "prod.terraform.tfstate" use_azuread_auth = true subscription_id = "00000000-0000-0000-0000-000000000000" tenant_id = "00000000-0000-0000-0000-000000000000" } }
backend "azurerm" { storage_account_name = "abcd1234" container_name = "tfstate" key = "prod.terraform.tfstate" access_key = "abcdefghijklmnopqrstuvwxyz0123456789..." } }
backend "azurerm" { storage_account_name = "abcd1234" container_name = "tfstate" key = "prod.terraform.tfstate" sas_token = "abcdefghijklmnopqrstuvwxyz0123456789..." } } Point to Consider:
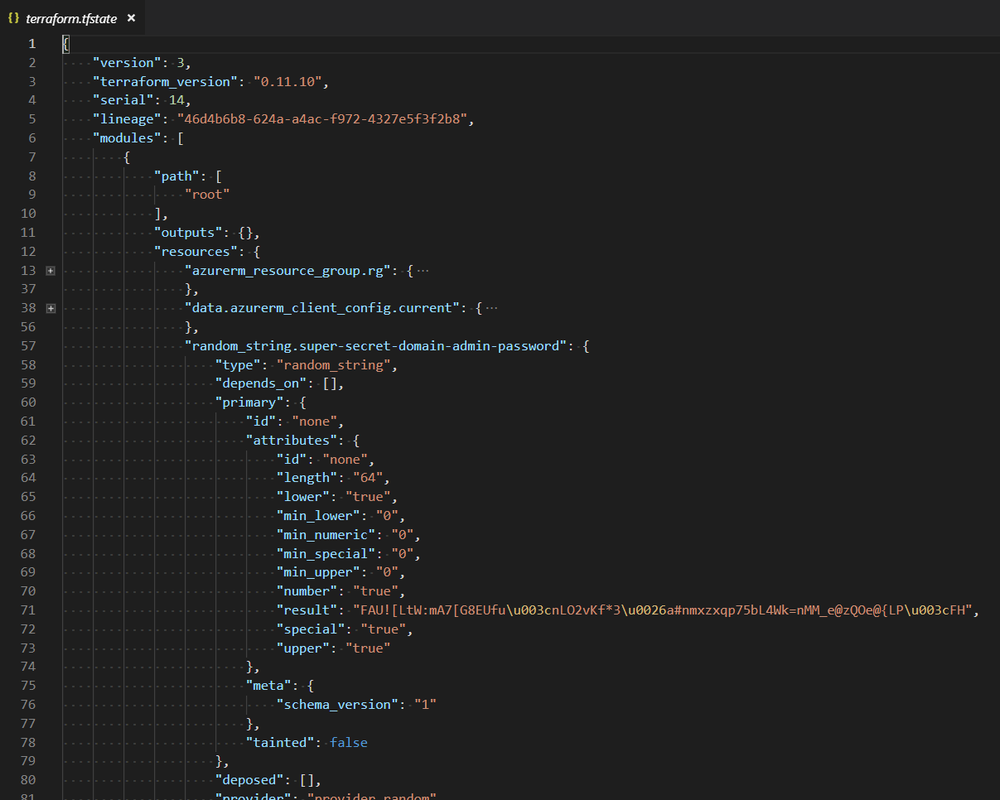
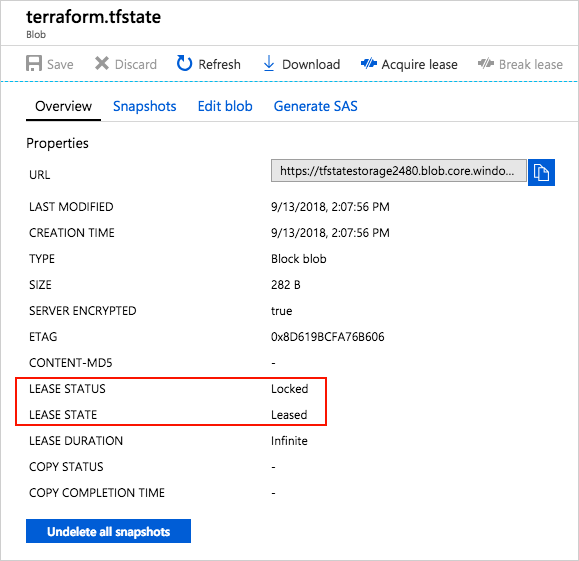
Full Code: terraform { required_providers { azurerm = { source = "hashicorp/azurerm" version = "=2.46.0" } } backend "azurerm" { resource_group_name = "azureheros-rg" storage_account_name = "azurehero-stg" container_name = "tfstate" key = "terraform.tfstate" } } provider "azurerm" { features {} } resource "azurerm_resource_group" "state-demo-secure" { name = "state-demo" location = "eastus" } Run the following command to initialize the configuration: terraform init Run the following command to run the configuration: terraform apply Listed below a useful command you can use to manage the state file e.g you can print the state file components What does it contain? After running terraform apply, the terraform.tfstate file will look something like this: Terraform State locking Azure Storage blobs are automatically locked before any operation that writes state. This pattern prevents concurrent state operations, which can cause corruption Security
Data stored in an Azure blob is encrypted before being persisted. When needed, Terraform retrieves the state from the backend and stores it in local memory. Using this pattern, state is never written to your local disk
0 Comments
Leave a Reply. |
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|



 RSS Feed
RSS Feed
