|
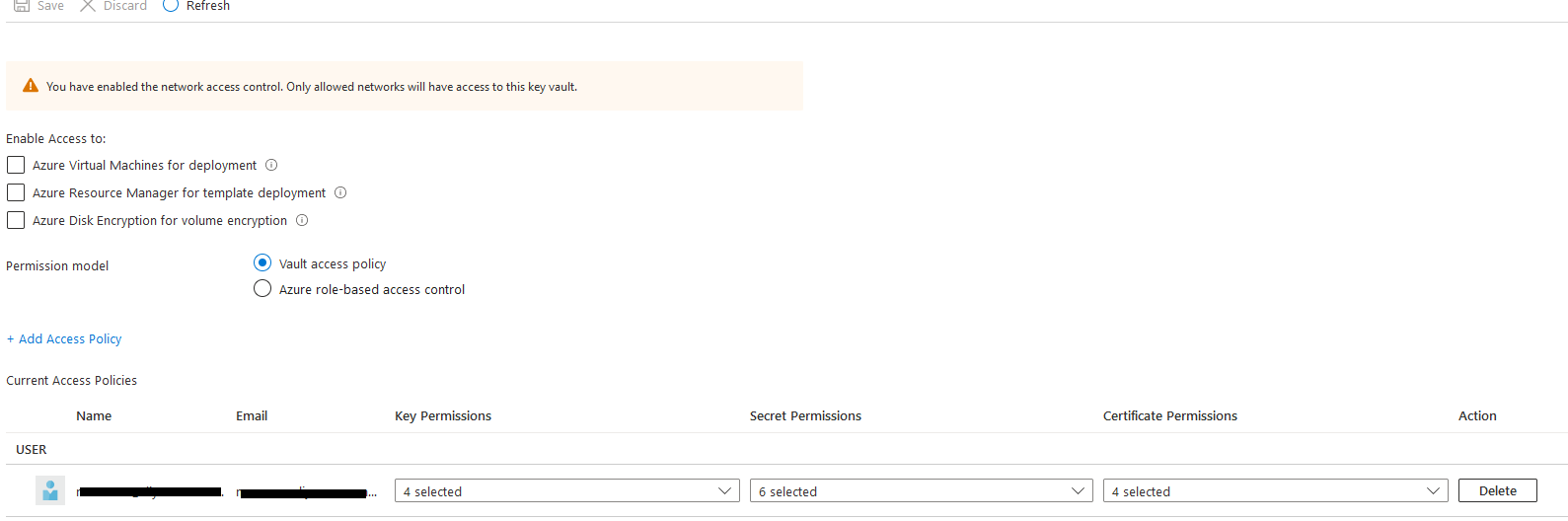
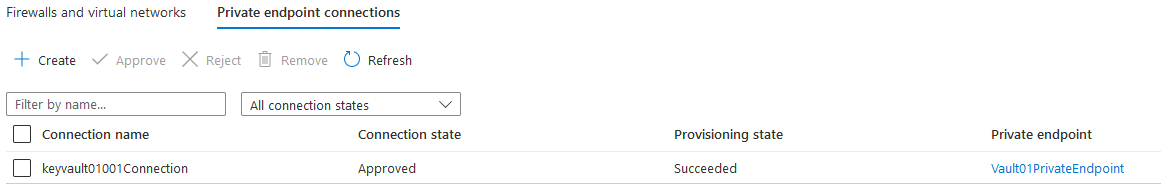
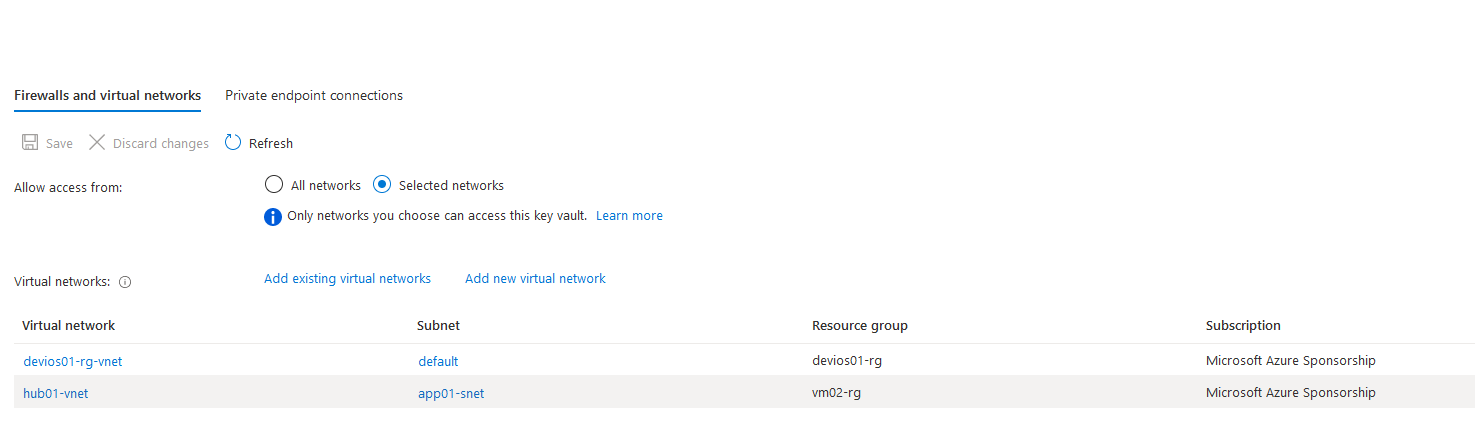
The purpose of Azure Key Vault is to store cryptographic keys and other secrets used by cloud applications and services in a HSM (Hardware security module). In this example, we will create and mange Azure Key Vault using Terraform First, we will create main configuration file for Key vault:
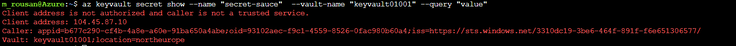
Variables File variable "name" { Result Proof that External Access is not allowd
1 Comment
Mrtin
2/1/2022 01:41:22 pm
Awsome
Reply
Leave a Reply. |
Author
Mohammad Al Rousan is a Microsoft MVP (Azure), Microsoft Certified Solution Expert (MCSE) in Cloud Platform & Azure DevOps & Infrastructure, An active community blogger and speaker.
Al Rousan has over 8 years of professional experience in IT Infrastructure and very passionate about Microsoft technologies and products. Top 10 Microsoft Azure Blogs
Archives
September 2023
Categories
All
|



 RSS Feed
RSS Feed
